Assets

Exchange

Buy Crypto

Products




Concordium is often mentioned alongside privacy-focused blockchains, but that comparison misses the point. Instead of offering full anonymity, Concordium was designed around regulated privacy, where identity and compliance are built directly into the protocol. This identity-first approach positions Concordium as a blockchain for real-world use cases, institutions, and regulated environments—while still preserving user privacy through cryptography. At the center of the ecosystem is CCD, the native token that powers transactions, staking, and network security.
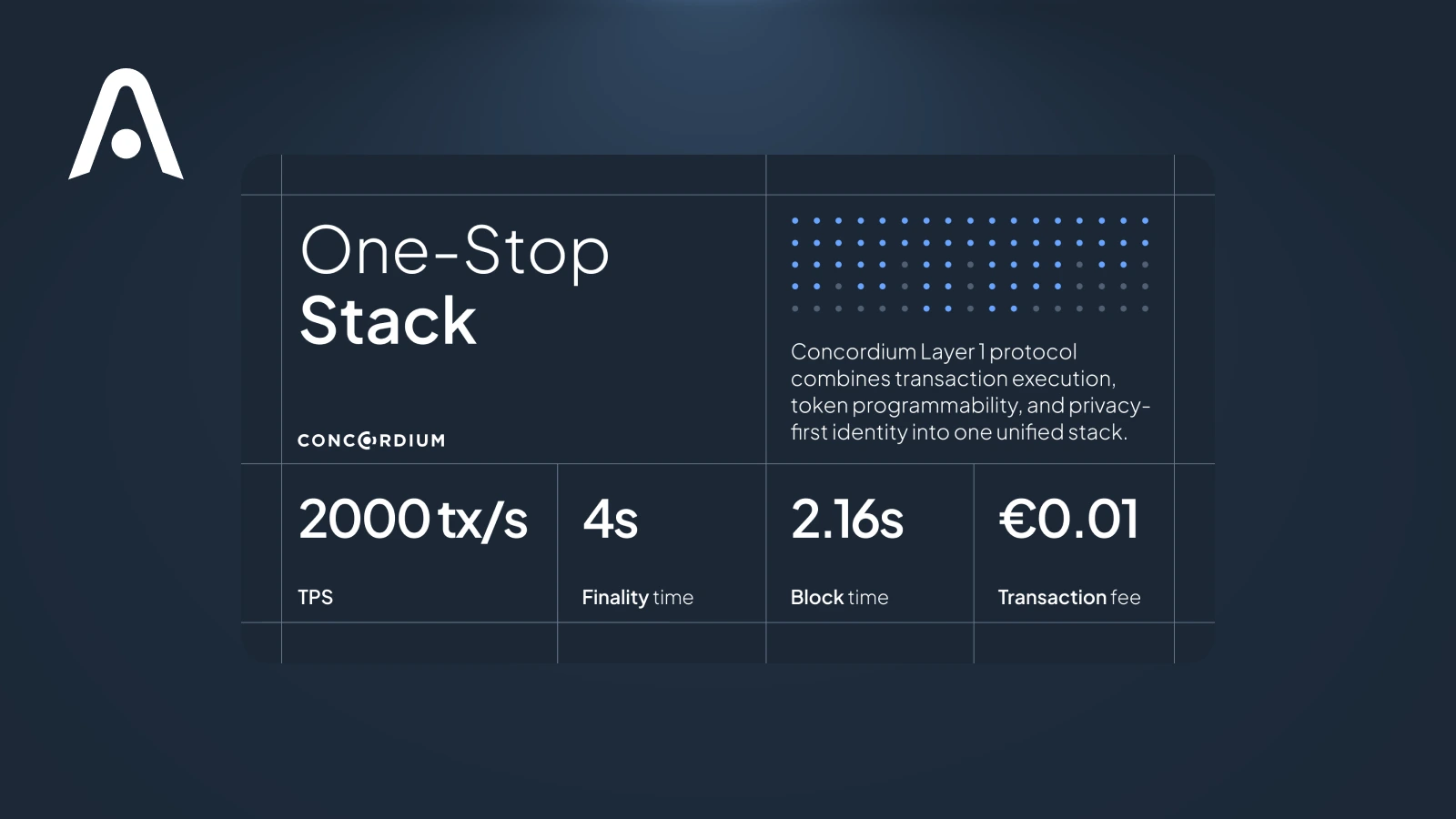
Concordium is a Layer 1 blockchain built specifically for environments where privacy and regulation must coexist. Rather than treating identity as an external add-on, Concordium integrates it directly at the protocol level.
Key characteristics of Concordium include:
This architecture allows Concordium to support privacy-preserving applications while remaining compatible with regulatory and compliance requirements—an approach that sets it apart from most other blockchain networks.
While Concordium uses advanced cryptography to protect user data, its approach to privacy is fundamentally differen from traditional privacy coins. The distinction lies in how identity, accountability, and regulatory compliance are treated at the protocol level.
Privacy on Concordium is implemented through an identity layer that operates alongside the blockchain rather than on top of it. Every account is associated with a verified identity, but that identity is not exposed onchain during normal transactions. Identity providers handle verification, while the blockchain only processes cryptographic proofs.
Zero-knowledge techniques are used to separate identity from transaction execution. This means users can interact privately, while the system still allows compliance when required. By designing privacy and identity as core protocol features, Concordium avoids retrofitting compliance later and instead treats regulation as a first-class design constraint from the start.
CCD is the native token of the Concordium network. It is not positioned as a privacy token or speculative asset, but as a utility token that supports the economic and security model of the blockchain.
CCD is used for several core functions:
The value of CCD is therefore tied to network usage and participation rather than anonymity features or narrative-driven demand.
Staking plays a central role in how Concordium secures its network and distributes incentives. The blockchain uses a proof-of-stake model where participants can either run infrastructure or delegate their stake to active validators.
Key aspects of concordium staking include:
This structure allows users to contribute to network security while earning protocol-level rewards, without relying on centralized intermediaries.
Buying CCD follows a standard flow used for most Layer 1 tokens, with an emphasis on moving funds into self-custody after purchase. The exact platforms may vary by region, but the process itself is straightforward.
Steps to buy Concordium (CCD):
Once CCD is in a non-custodial wallet, users have full control over their tokens and can participate in network features such as staking without relying on centralized platforms.
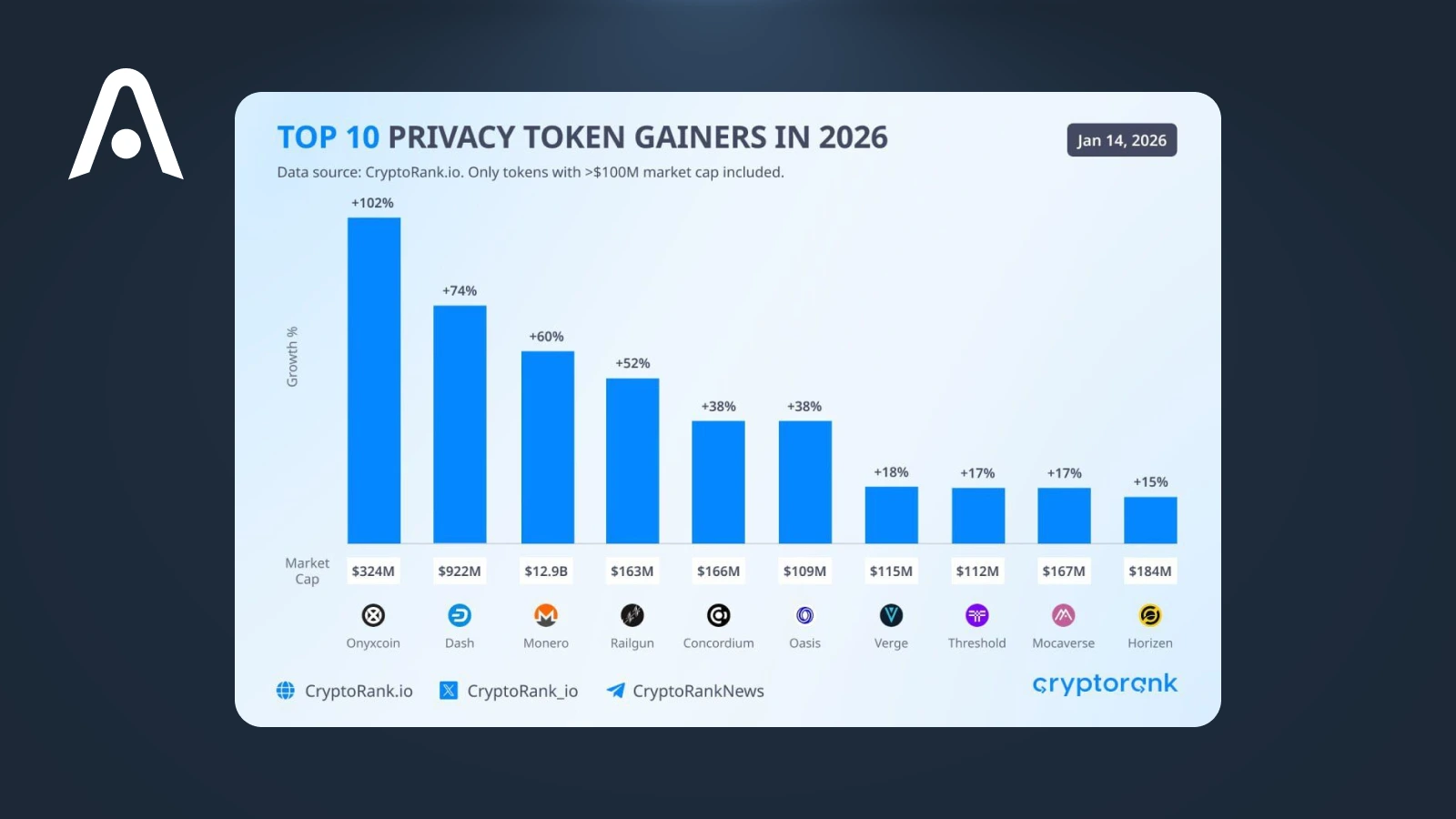
Interest in Concordium has increased alongside renewed discussions around privacy in crypto—but for a different reason than most privacy-focused projects. As regulatory pressure grows, fully anonymous blockchains face increasing friction, while demand rises for alternatives that balance privacy with accountability.
Concordium fits into this gap. Its compliance-first design, identity layer, and selective disclosure model position it as an alternative path for projects and institutions that need privacy without breaking regulatory constraints. Rather than riding the privacy coin narrative directly, Concordium is gaining attention by offering a model that aligns with real-world legal and institutional requirements.
Concordium is often compared to privacy coins, but the differences are structural rather than cosmetic. While both approaches use cryptography, their goals and trade-offs are not the same.
Key differences include:
This makes Concordium less attractive to users seeking absolute anonymity, but more suitable for enterprises, institutions, and applications that must operate within legal frameworks.
CCD is best understood as a utility token tied to a compliance-oriented blockchain rather than a narrative-driven privacy asset. Its role is to support transactions, staking, and governance within the Concordium network.
Before using CCD, it is important to understand that adoption depends on real-world use cases, regulatory alignment, and institutional interest. Like any blockchain token, CCD carries market risk and volatility, but its long-term relevance is closely linked to whether compliance-first blockchain infrastructure gains broader traction beyond experimental crypto environments.
Using CCD effectively starts with proper self-custody. Holding CCD in a non-custodial wallet allows users to maintain full control over their assets while deciding whether to simply store tokens or participate in concordium staking directly from their own wallet.
Atomic Wallet supports secure self-custody for CCD, enabling users to store tokens, manage balances, and prepare assets for staking participation without relying on centralized platforms. This approach keeps control in the hands of users while supporting long-term interaction with the Concordium ecosystem.

Learn what StakeShark is and how non-custodial staking validators work. Understand PoS delegation, slashing risks, uptime, supported networks, and how to stake crypto securely.